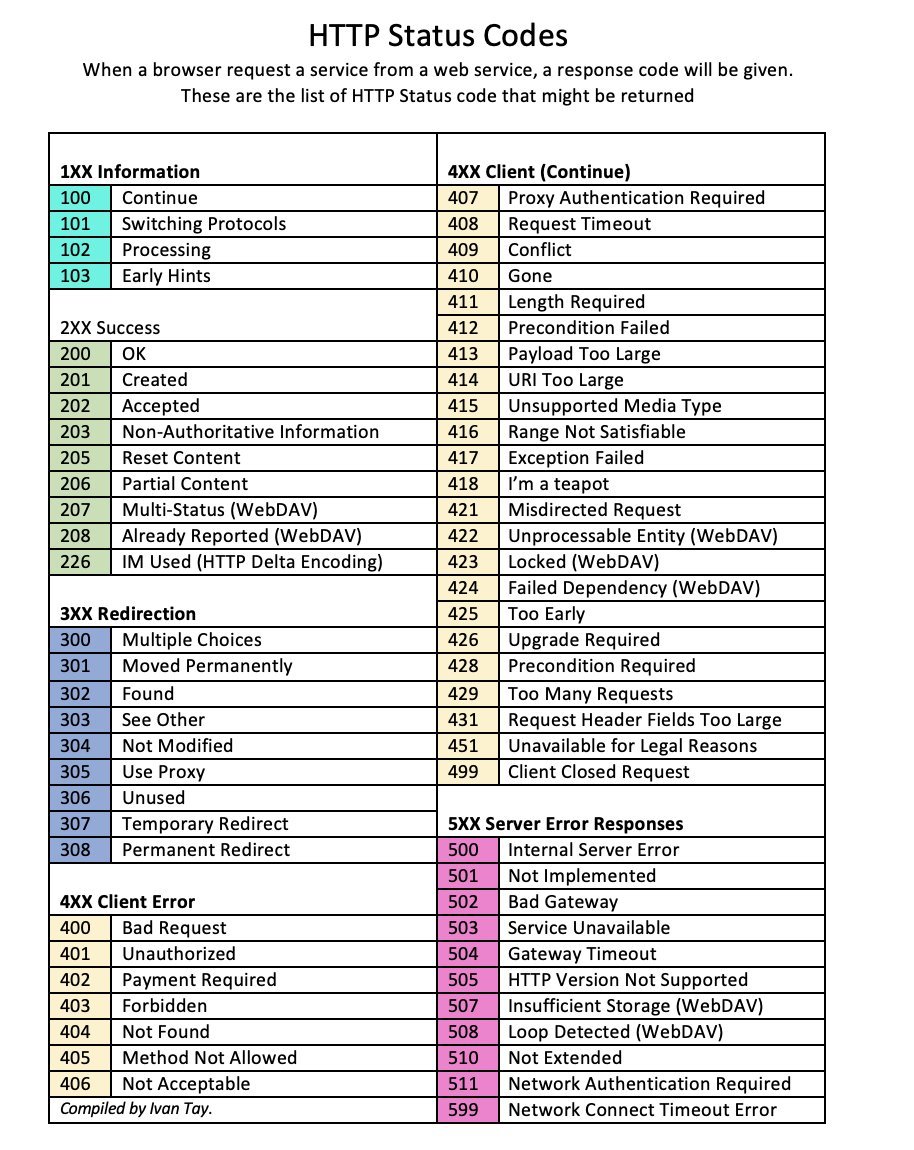
How Hackers Can Become Persistent Threats
An academic analysis of website defacement behavior by 241 new hackers shows there are four clear trajectories they can take in future, researchers say.

Tracking malicious hackers' early activities using open source intelligence can offer substantial clues about the likelihood of their becoming a persistent threat in the future, two university researchers claimed in a report this week.
That knowledge can help guide early intervention efforts to nudge fledgling hackers off their criminal trajectories, they noted.
Christian Howell, assistant professor in the Department of Criminology at the University of South Florida, and David Maimon, a professor at Georgia State University's Department of Criminal Justice & Criminology, recently tracked 241 new hackers engaged in website defacements for a period of one year.
Today, adversaries generate 100 million new malware samples per year. Because they all require manual coding, it is still a finite, manageable amount for signature detection. With ChatGPT, however, a hacker can say, "Here's what I'm trying to do, and here's the OS I'm trying to do it on," and it can generate hundreds of thousands of iterations of one piece of malware.
This will mean that the detection engines' ML models must be recomputed faster. It's far more complicated, because they're working against a much larger data set. Fortunately, ChatGPT will supercharge the reverse-engineering process and give anti-malware efforts a fighting chance.
For instance, a significant reverse engineering challenge is working with a generic file name, which doesn't provide necessary context about where it was found. This requires much more manual work to identify the system for which it was built. There are minor changes in binary assembly that have marked changes on the end result — e.g., was it written for a 32-bit or 64-bit architecture? Is the system using Little Endian or Big Endian? The answers determine the direction in which you read the machine language (forward or backward).
All these efforts require trial and error if you have no context. ChatGPT can run through these iterations at blazing speed and give reverse engineers the final assembly language and process it from there. They can take it further and have ChatGPT tell them what it thinks the application is doing — in natural language. More importantly, ChatGPT could do all of this at scale, analyzing hundreds of thousands of binary samples and proving insights to an analyst.
It also can help fight back against common cat-and-mouse techniques. For example, malware often contains anti-reverse engineering techniques, such as nested loops, to make it much harder for reverse engineers to keep track of what is happening and the end state. ChatGPT can figure that out much faster than humans. It also can analyze the genetic code of the malware and see where there may be code reuse to identify the fingerprint of the author more quickly.
Long-Term Implications
Whenever new advances in AI come to fore, there is the inevitable concern about whether it will replace humans and their jobs. I don't believe ChatGPT will make this happen, but it will make us more powerful consumers of information. The force multiplier effect will be profound at all levels. I can see CISOs feeding it a set of information about its risk register for it to return policies and procedures, incident response plans, and more — all tailored to their environments.
While ChatGPT is only a research preview, I share the excitement of my industry colleagues about its promise to revolutionize how security practitioners work.
Early Intervention for Fledgling Hackers
Howell and Maimon identified hackers as new for their study based on information the individuals posted on Zone-H, a platform that malicious actors widely use to report website defacements. Hackers basically upload evidence of their attack, including their moniker, the defaced website's domain name, and an image of the defaced content to Zone-H. Once administrators there verify the content, they post the information to the archive, where it is publicly viewable. Zone-H currently maintains records of more than 15 million attacks that have resulted in website defacements over the years.
The two researchers tracked each of the hackers for a period of 52 weeks from their first disclosed website defacement on Zone-H. Because many attackers use the same online aliases across platforms to establish their reputation and status, the researchers were able track them across multiple environments, including social media channels such as Facebook, Twitter, Telegram, and YouTube.
"Based on a hacker's behavior in the first few months of their career, you can predict where they are going to be further on in their career," Maimon says. "We can definitely nudge these actors away from a life of cybercrime," by intervening early, he adds.
Maimon points to previous research that he was part of, along with Howell and another researcher, that showed early intervention can have an impact on budding criminal behavior. In the study, the researchers — purporting to be hackers themselves — sent direct messages to a selected group of hackers about alleged lawenforcement efforts targeting those involved in defacement activity. The messages prompted many of those who received them to cut back their defacement activity, apparently out of concern about law enforcement tracking them down, he says.
Four Distinct Trajectories
They collected information about the total number of attacks that each hacker carried out during the one-year period, analyzed the content of their website defacements, and gathered open source intelligence about the hackers from social media and underground sites and forums.
The data showed that 241 hackers defaced a total of 39,428 websites in the first year of their malicious hacking careers. An analysis of their behavior revealed that new hackers follow one of four trajectories: low threat, natural desisting, increasingly prolific, and persistent.
A plurality of the new hackers (28.8%) fell into the low-threat category, which basically meant they engaged in very few defacements and did not increase their attack frequency through the year. Some 23.9% were naturally desisting, meaning they began their careers with substantial velocity but then appeared to lose interest quickly. Hackers in this category included politically motivated hacktivists who likely lose sight or got bored of their cause, the researchers surmised.
Hackers in the more troublesome categories were the 25.8% who engaged in an increasing number of attacks over the course of the year and the 21.5% in the persistent category who started with a substantial number of attacks and maintained that level through the year.
"Increasingly prolific hackers engage in more attacks as they advance in their career, while persistent threats continually engage in a large number of attacks. Both are problematic for system admins," Howell says. He notes that it's hard to say for sure what percentage of the hackers in the study engaged in other forms of cybercrime besides website defacements. "But I found several selling hacking services on the Dark Web. I suspect most — if not all — engage in other forms of hacking."
Telltale Signs
The two researchers found that hackers who had a high level of engagement on social media platforms and reported their website defacements to multiple archives tended to also be the more persistent and prolific actors. They also tended to disclose their aliases and ways to contact them on sites they defaced. Howell and Maimon chalked the behavior up to attempts by these actors to establish their brand as they prepared for a long-term career in cybercrime.
Often, these actors also indicated they were part of broader teams or became part of a broader group. "New hackers are typically recruited by existing teams with more sophisticated members," Howell says.
The study showed that cyber intelligence from publicly available sources is useful in forecasting both threats and emerging threat actors, Howell says. He notes that the focus now is on developing AI algorithms that can help improve these forecasts going forward.
What's Your Reaction?