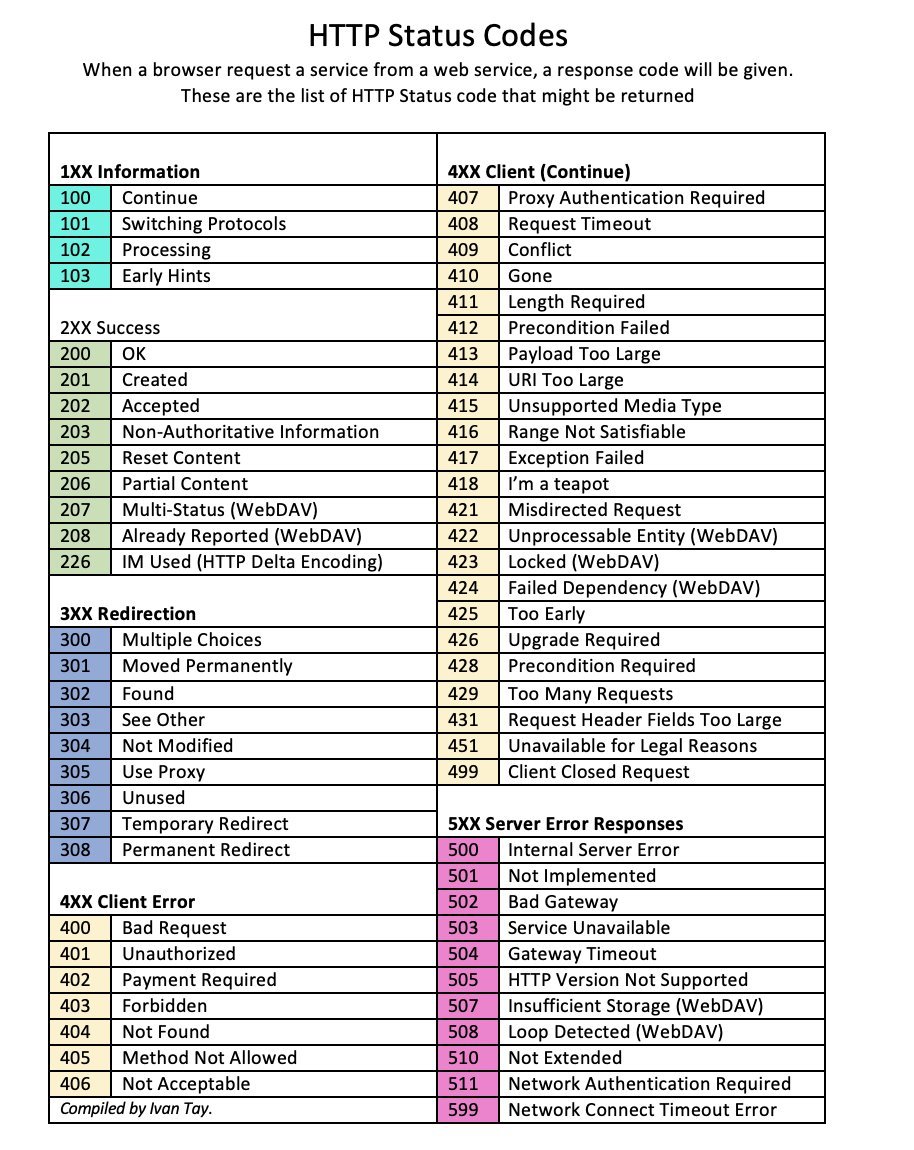
Penetration Testing Service
Penetration testing (pentest) is an authorized cyber attack, performed to evaluate the security of a website, server or application. During pentest, we attempt to find vulnerabilities that could be exploited by a malicious attacker in order to sabotage your system, steal confidential data, or otherwise compromise your system. As penetration testers, we attempt to put ourselves in the shoes of an attacker, and perform reconnaissance and attacks similar to those used by real attackers, but without any intent to cause harm. When we finish, we present our clients with a detailed report on the vulnerabilities we found during the test and how to mitigate them.
There are three broad categories of penetration testing:
1. Whitebox
Whitebox, also known as internal penetration testing, where the testers have access to source code, detailed specifications, and other kinds of information not normally available to a malicious hacker. This information can help us identify hidden vulnerabilities that we could have otherwise missed.
2. Graybox
Graybox, where the testers only have limited access to useful confidential information.
3. Blackbox
Blackbox, or external penetration testing, where the testers are in the dark, faithfully simulating a typical attack. This kind of testing forces the penetration testers to use the exact same tools as an attacker, and can therefore be useful for finding practical vulnerabilities an attacker would come across. It is also important to note that penetration testing can be done on any kind of exposed system, including but not limited to applications, servers, websites, and programs.
Our penetration tests are designed to meet the most stringent compliance requirements, such as SOC2, ISO27001, HIPAA. Our team of experts follows the industry standard of OWASP testing while accommodating our clients’ specific needs.
Our basic penetration test package includes a comprehensive risk assessment of our clients’ business, vulnerability scans, and manual security audits. This suite of services in combination with our compliance reports ensures complete cybersecurity protection and compliance for our clients.
Our reports are hand-tailored to our clients’ specific needs. Our reports include an OWASP standard technical analysis of the penetration test, following a user-friendly detailed explanation of our findings.