Recommended Tools for CTF
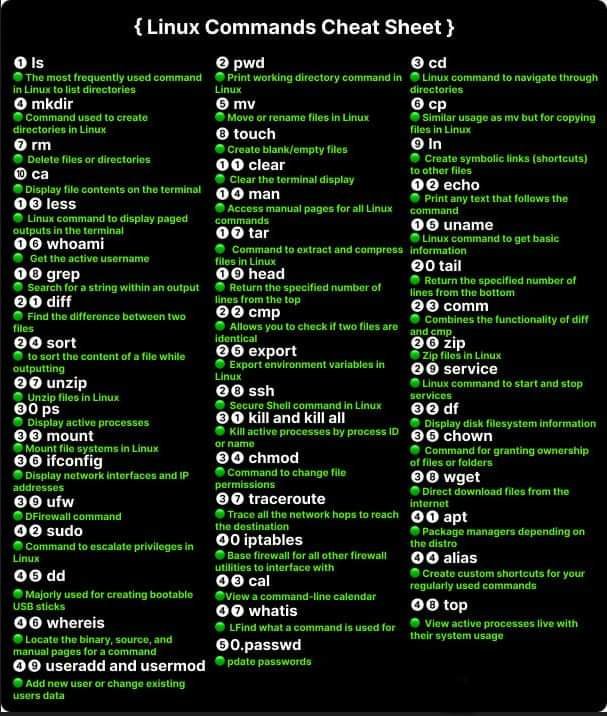
In addition a knowledge of basic Linux commands, access to the following tools (or equivalent tools) are recommended as preparation for an entry level Capture-the-Flag (CTF) competition. Use what ever works for you!

- General Competition Tools:
- Basic Linux Commands
- Kali Linux
- Google Chrome SSH – Lightweight SSH Browser addon:
- Number / Text Conversion Tools:
- Number Converter ( Binary, Octal, Decimal, Hex)
- Hex to ASCII (text)
- Binary to Text
- Text to Numbers (Hex, Decimal, Binary)
- Base64 (Text, Hex, Video, Audio, etc. )
- Base2-Base36 – Base2 to Base36 Converter
- Open Source Intelligence:
- Google, Google Maps, Google Dorks (operators)
- whois.domaintools.com – Domain owners, name servers info, IP addresses
- www.robtex.com – Host name, IP , DNS and registry information
- Jeffrey’s Image Meta Data Viewer – Image Meta Data info
- Steganography Tools:
- StegOnline – web-based open-source port of StegSolve.
- Hex Editor – browser based hex editor
- ‘strings‘ – Linux command to view visible text characters
- ‘binwalk‘ – Linux command to extract embedded files and executables
- Digital Invisible Ink Toolkit – hide/extract files from inside an image
- Steghide – open source steganography software (Linux)
- Stegosuite – a free steganography tool written in Java (Linux).
- pngcheck – look for/correct broken chunks.
- GeorgeOM.net – Geo Explore Colour & Bit Planes (Go to “Browse Bit Planes”)
- Crytography Decoders:
- XOR Decorder – Calculate exclusive ‘OR’ operation
- Caesar Cipher – Shift Cipher
- ROT13 – Shift Cipher
- A1Z26 – Replace Letters with Numbers
- Vigenere Cipher (requires a key)
- Atbash Cipher (simple)
- Vernan (One-time Pad)
- Rail Fence Cipher (ZigZag)
- Password Cracking:
- Hash-Identifier – Identifies hash type (Kali)
- Hashcat – HASH cracking tool (Kali)
- Crackstation – Browser based Hash Cracker: (https://crackstation.net/)
- md5sum – calculates/verifies 128-bit MD5 hashes,
- John the Ripper – Detect and crack weak PWs (Kali).
- Rockyou.txt WordList (download) – contains 14m unique PWs (Kali).
- Web Exploitation:
- /robots.txt – lists pages or files that search engines can’t request,
- Dirbuster – brute force discovery of hidden directories/files (Kali)
- Development Tools – Browser option use to inspect source and cookies.
- User Agent Extension – allows browser to switch user agent .
- Log Analysis:
- Scanning:
- Nmap – utility for network discovery and auditing
- Dirbuster – Scan web sites for hidden web pages
- Metasploit Framework – scan for known vulnerabilities (Kali)
- Recon-ng – perform recon on remote targets (Kali).
- W3bin.com – Info on who is hosting a website
- Network Traffic Analysis:
- Wireshark – GUI based traffic capture and analysis tool (Kali, Windows or Mac OS).
- tcpdump – packet analyzer utility for Linux command line
- WinDump – Windows version on tcpdump.
- ngrep – search for strings in network packets
- Enumeration and Exploitation:
- ‘File’ Command – determine a file type (including executables)
- ‘Strings’ Command – Display text comments in an executable.
- Hex Editor – view executable for visible text stings
- ‘xxd -r’ Command – convert a hex dump back to its original binary form
- Ghidra – reverse engineering tool developed by the NSA
- Objdump -d – Linux command line dis-assembler
- Netcat – utility that reads and writes data across network
- uncompyle6 – translates Python bytecode back into source
- GDB – Inspect memory w/in the code being debugged
- Pwntools – a CTF framework and exploit development library.
- Wireless Exploitation:
- Wigle.Net – Wifi info database for hotspots from around the world
- Kali Linux – Linux suite of cybersecurity tools
- Wireshark – network packet analysis
- Aircrack- ng – tools to assess WiFi network security
- ‘ifconfig‘ command – configure and query TCP/IP network interface parameters
- Stumbler (set SSID to ANY) active mode (Windows)
- Kismet : both war-drive and sniffer. Uses passive mode (Linux)
What's Your Reaction?