Windows Red Team Privilege Escalation Technique
Windows Red Team Privilege Escalation Techniques - Bypassing UAC, Kernel Exploits & Token Impersonation
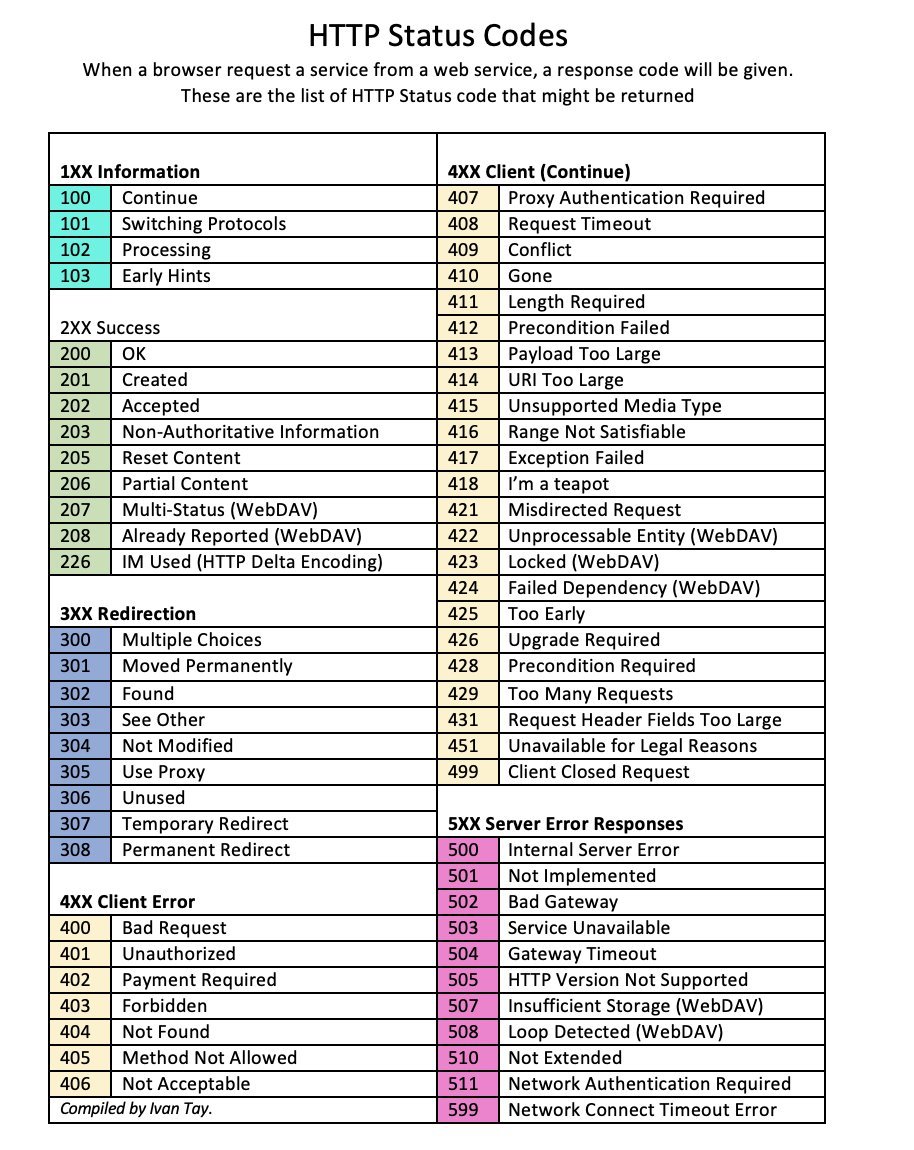
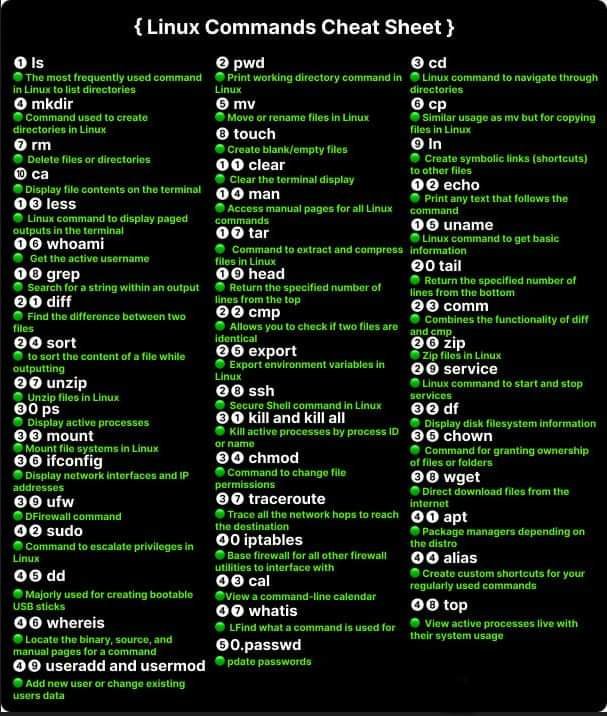
In this video, I will be exploring the process of privilege escalation on Windows by leveraging various privilege escalation techniques. Privilege Escalation consists of techniques that adversaries use to gain higher-level permissions on a system or network. Adversaries can often enter and explore a network with unprivileged access but require elevated permissions to follow through on their objectives. Common approaches are to take advantage of system weaknesses, misconfigurations, and vulnerabilities.
#infosec #infosecurity #redteam #pentesting
What's Your Reaction?