This site uses cookies. By continuing to browse the site you are agreeing to our use of cookies Find out more here
Slaytec
Pentester, Senior Offensive Security Consultant, Senior Security Researcher
Top 20 Bug Bounty YouTube Channels of 20...
Let's look back at 2022 and specifically at the creators who ruled the bug bounty scene in 2022. These are the top 20 bug bounty ...
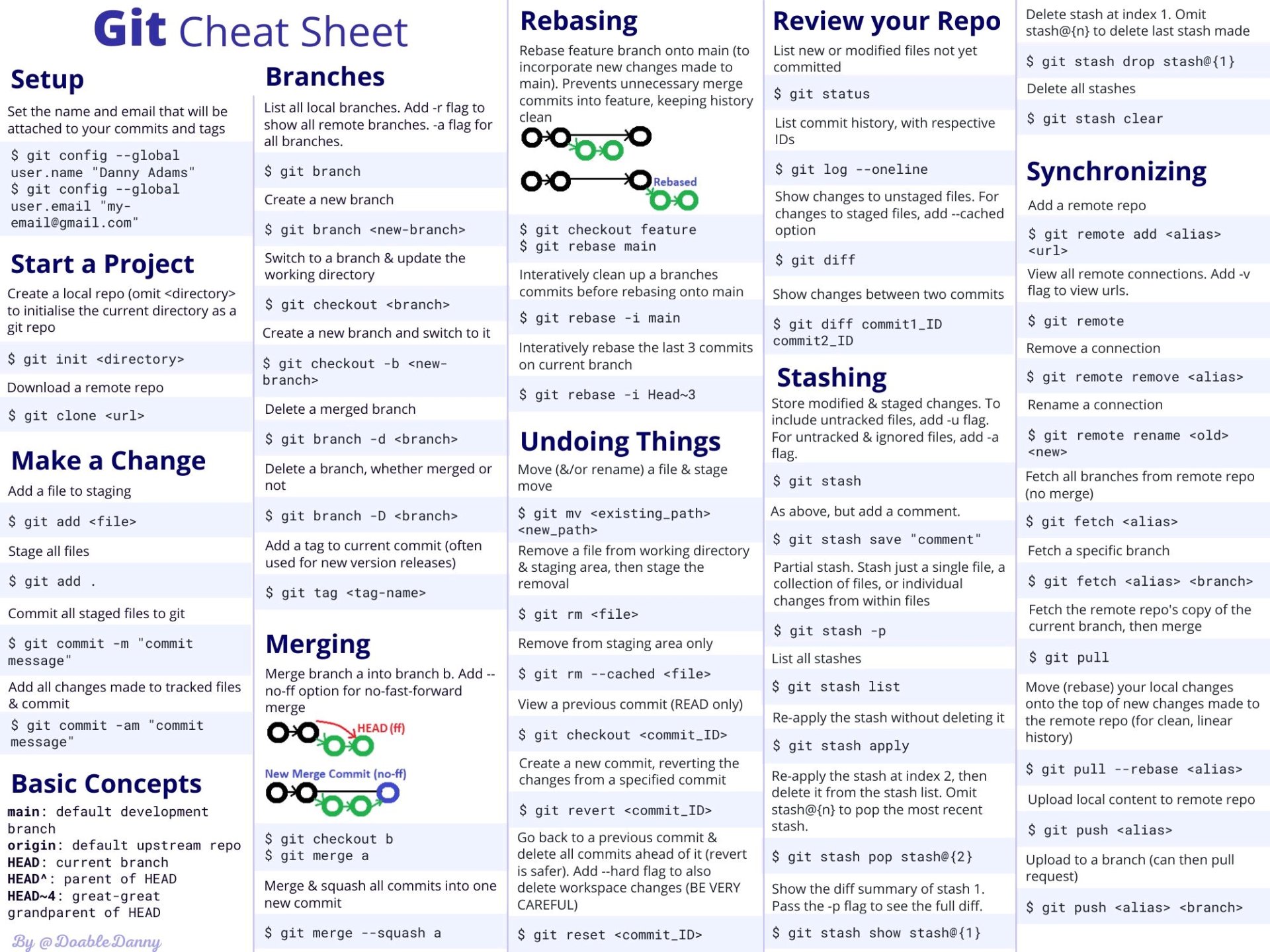
GIT Command Cheat Sheet
GIT Commands
Tools and Techniques for Red Team / Pene...
This github repository contains a collection of tools and resources that can be useful for red teaming activities.
ChatGPT For Cybersecurity
In this video, HackerSploit go over the process of how to use ChatGPT and cover various examples of how to use ChatGPT for Cyberse...
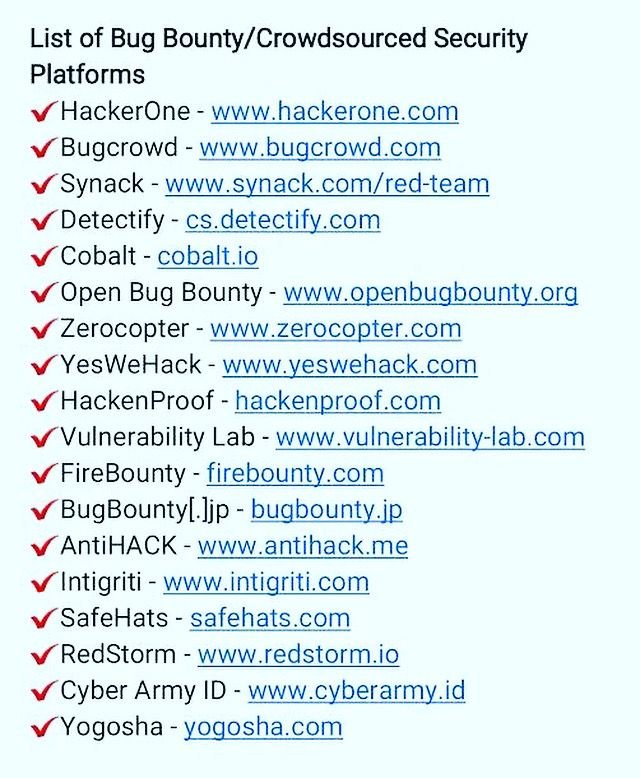
List of Bug Bounty Platforms
Bug Bounty & Crowdsourced Security Platforms
OSCP Reborn - 2023 Exam Preparation Guid...
Revamped OSCP guide, tailored to be relevant for the latest revision of the OSCP which includes Active Directory exploitation.
Facebook to Pay $725 Million to settle L...
Meta Platforms, the parent company of Facebook, Instagram, and WhatsApp, has agreed to pay $725 million to settle a long-running c...
Thousands of Citrix Servers Still Unpatc...
Thousands of Citrix Application Delivery Controller (ADC) and Gateway endpoints remain vulnerable to two critical security flaws d...
Hacking websites with Burp Suite
Learn the basics of burpsuite. Start using Burp with web applications.
Cross-Site Scripting (XSS) Explained And...
Cross-Site Scripting (XSS) Explained And Demonstrated By Loi Liang Yang - Ethical Hacker, Penetration Tester and Cybersecurity Con...
Kali Linux Commands (A-Z)
Kali Linux Commands Cheat Sheet
Shell Uploading in Web Server through Ph...
In this tutorial, we will learn how to exploit a web server if we found the phpmyadmin panel has been left open. Here I will try t...