This site uses cookies. By continuing to browse the site you are agreeing to our use of cookies Find out more here
How File Upload Vulnerabilities Work
Learn about File Upload vulnerabilities. In this video, we are going to learn about ways on how to exploit file upload vulnerabili...
Windows Red Team Privilege Escalation Technique
Windows Red Team Privilege Escalation Techniques - Bypassing UAC, Kernel Exploits & Token Impersonation
ZAPROXY - Advanced Scan XSS
ZAPROXY - Advanced Scan XSS - HACKING TUTORIALS (OWASP ZAP)
OSINT Tools for Hacker
OSINT Tools for Hacker
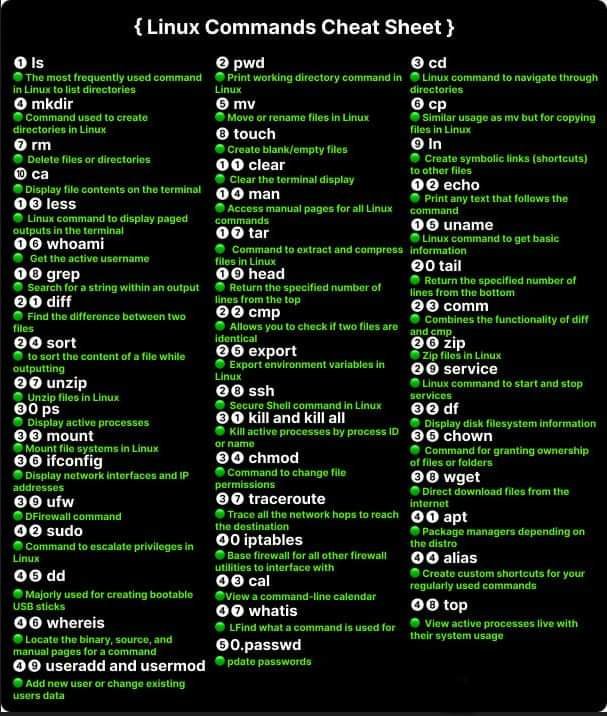
Linux Command Cheat Sheet
Linux Command Cheat Sheet
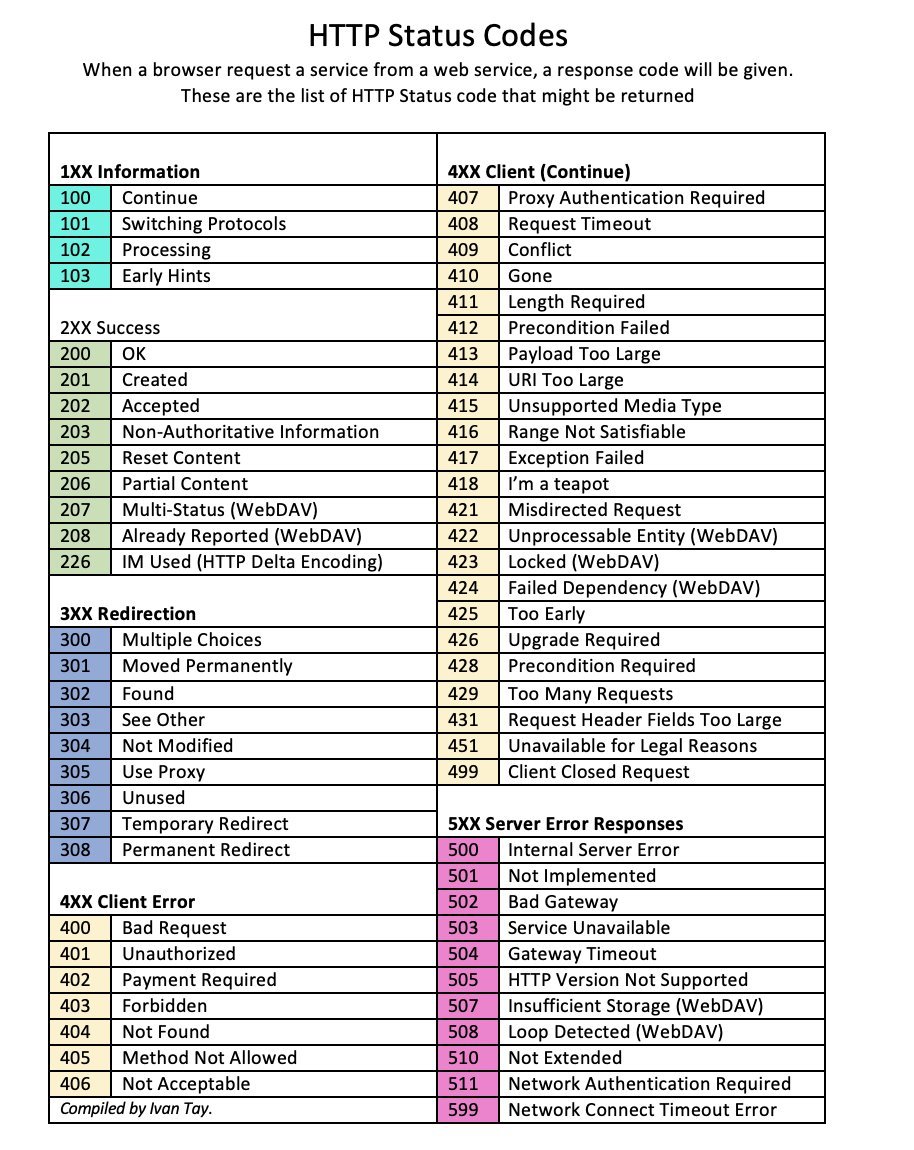
HTTP Status Code
HTTP Status Code
Remotely Control Any PC in 4 mins 59 seconds
Loi Liang Yang - Ethical Hacker | Penetration Tester | Cybersecurity Consultant show us how control any pc in 4 mins.