This site uses cookies. By continuing to browse the site you are agreeing to our use of cookies Find out more here
Ransomware attack hit KFC and Pizza Hut stores in ...
Nearly 300 fast food restaurants, including branches of KFC and Pizza Hut, were forced to close following a ransomware attack agai...
Advanced Phishing Methods
Phishing attacks are becoming increasingly sophisticated. Adversaries are using advanced techniques to evade detection and trick i...
Cellebrite and MSAB software leak
Data from Cellebrite & MSAB, two companies that provide phone hacking tools to governments, has just been published online. The le...
Starting Bug Bounty in 2023!
This video is for those folks that are gearing up to start their bug bounty journey in 2023!
Python for Everybody - Full University Python Cour...
This Python 3 tutorial course aims to teach everyone the basics of programming computers using Python. The course has no pre-requi...
Russian threat group using other crooks malware to...
A suspected Russian threat group is believed to have begun targeting victims in Ukraine, piggybacking off previously deployed malw...
How To Use Phone as Multi Bootable USB Drive!
Turn Android Phone Into a Bootable USB Drive! How to use Android phone as a bootable USB drive? It may sound a little weird, but i...
CISSP Certification Course – PASS the Certified In...
CISSP is one of the most valuable Cyber Security Certificates in the market today. This course will qualify you to pass the CISSP ...
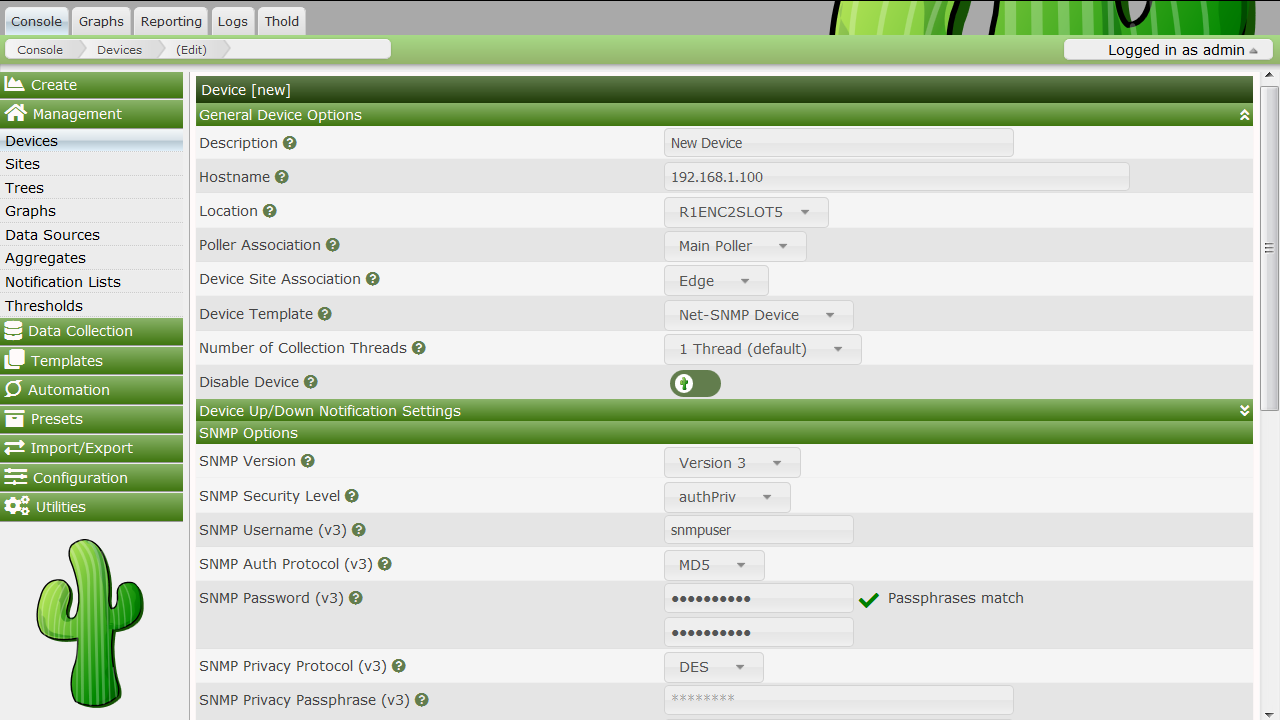
Unauthenticated Remote Code Execution in Cacti
Cacti is an open-source, web-based monitoring solution with a long-standing history dating back to its first release in 2001. Nowa...
WordPress Security Alert
A new strain of Linux malware is targeting WordPress sites, taking advantage of vulnerabilities in various plugins and themes to i...
2023 Path to Master Hacker
This is your path to becoming a master hacker. From zero to getting the skills you need to be successful.
Recommended Tools for CTF
In addition a knowledge of basic Linux commands, access to the following tools (or equivalent tools) are recommended as preparatio...